Information Security
Initiatives to Ensure Information Security
Goals and Achievements of Major Initiatives
Establish a global information security framework.
| Goal for fiscal year 2023 | Based on the information security road map devised in fiscal year 2022, decisively implement action plans for themes determined to be of particular importance. Minimize information security risks in a global and open cloud-based digital environment, strengthen ability to address incidents when they occur and to minimize the impact thereof. |
|---|---|
| Achievements in fiscal year 2023 |
|
| Evaluation | ★★ |
| Goal for fiscal year 2024 | Based on the information security road map, continue to decisively implement action plans for themes determined to be of particular importance. Minimize information security risks in a global and open cloud-based digital environment, strengthen ability to address incidents when they occur and to minimize the impact thereof. |
- Evaluations are based on self-evaluations of current progress.
Key: ★★★ = Excellent; ★★ = Satisfactory; ★ = Still needs work
Basic Approach to Information Security
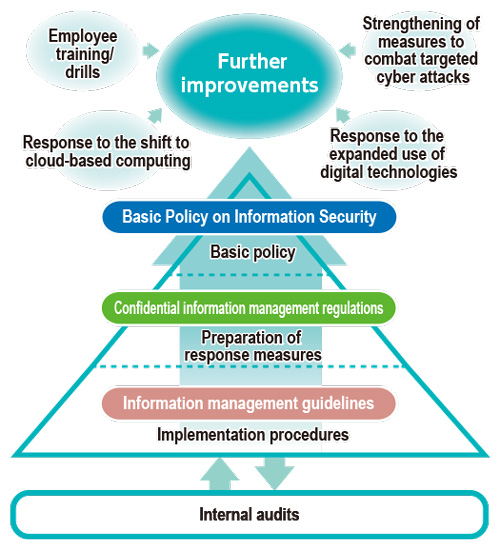
The DIC Group has positioned information security as a key management priority and established the Basic Policy on Information Security, which is founded on its recognition that protecting information assets that belong to or are managed by the Group is essential to its ability to conduct business. The DIC Group works to ensure that directors and employees use the Group’s information assets properly in the course of business and handle confidential information appropriately. The Group also pursues continuous improvements by conducting internal audits to confirm current issues and identify risks.
Promoting and Enhancing Information Security on a Global Basis
The DIC Group’s approach to information security management rests on four pillars: Regulations and guidelines, management framework, information security infrastructure, and employee education and training.
Regulations and Guidelines
In line with its Basic Policy on Information Security, in Japan, the PRC and the Asia–Pacific region the DIC Group has set forth confidential information management regulations, which stipulate the scope of management and related standards, rules and responsibilities, and the confidential information management guidelines, which outline procedures for implementation, as well as its information and communications technology management guidelines, which govern the management of information and communications technology environments. These are updated regularly and as required to address new security risks in a timely manner. The Group has also created and revises global guidelines and rules governing the use of AI, cloud computing and control systems in response to the increasing prevalence of digital technologies.
Management Framework
The Information Security Committee, which is led by the head of the IT Strategy Unit, meets regularly (twice annually) and whenever necessary as part of a system to facilitate the timely update of rules and guidelines to accommodate new technologies and risks, and to ensure changes are communicated effectively across the DIC Group. The committee formulates annual targets and initiatives for strengthening information security with the approval of the Sustainability Committee and manages the progress of related efforts.
Information Security Infrastructure
The DIC Group has formulated a road map for information security that focuses on latent risks identified through a risk assessment conducted by a third-party organization. Guided by this road map, the Group is advancing initiatives designed to permanently reduce related management and business risks by equipping it to respond swiftly and accurately to increasingly active and sophisticated cyber security threats. The Group is also working to enhance control systems management at individual sites by promoting the effective use of guidelines, as well as the determination of management cycles, to address issues identified through risk analysis and audits.
Going forward, the DIC Group aims to deploy information security measures introduced in Japan (including introducing internet security and endpoint security systems) elsewhere in Asia, as well as to strengthen its cyber attack detection and analysis capabilities in the Americas and Europe. In addition, the Group will plan and implement IT-related initiatives to streamline and automate related operations.
Employee Education and Training
The DIC Group offers an e-learning information security program for employees with access to information, whether online or offl ine. Given the increasingly advanced nature of cyber attacks and crimes, the Group also promotes ongoing efforts to improve employees’ awareness of information security and ability to respond effectively should an issue arise, including providing training in how to contend with phishing attacks.
Customer Privacy and Customer Data
To date, there have been no substantiated complaints regarding breaches of customer privacy and no incidents of leaks or the loss of customer data.
COMMENT
This is my view of DIC’s information security capabilities as a partner for DIC.

In addition to forensic services,*1 Verizon Japan Ltd. periodically provides DIC with security advisory services. To be precise, in addition to responding to queries pertaining to topics proposed by the Company, we also extend services designed to help fortify DIC’s security systems and enhance its knowledge base, including presenting case studies based on initiatives promoted by other companies and useful materials pertaining to risks associated with new technologies and approaches to strengthening security systems, as well training pertaining to settings for security devices, the basics of evidence preservation and the use of related tools, and how to address incidents when they occur.
DIC has one group that explores and implements effective security policies and governance and another that is responsible for technologies for the practical application of both to concrete solutions such as firewalls and endpoint detection and response (EDR) solutions. However, rather than being siloed off from each other, these groups cooperate and communicate, allowing them to maintain a constructive relationship that underpins the implementation of various initiatives. This is made possible by the fact that everyone involved is firmly focused on the same goal.
Looking ahead, it is my hope that we can continue to assist DIC in its efforts to build and maintain an ever-better security system through effective interactive collaboration.
- In the context of information security, forensic services support the ability to resolve security incidents such as unauthorized access and information leaks.
- EDR is a cybersecurity technology that providing detection and notification of cyber attacks on endpoints in an environment, such as computers, servers and smartphones.
Consultant, Verizon Japan Ltd. Yasuki Kono
Document Download